Advanced Rate Limiting
Defend your applications and APIs against abuse by throttling traffic that exceeds defined limits
Rate Limiting protects against denial-of-service attacks, brute force login attempts, traffic surges, and other types of abuse targeting APIs and applications.
BENEFITS OF RATE LIMITING
Mitigate DDoS attacks
Stop high-precision layer 7 attacks with granular configuration options.
Ensure API availability
Identify abusive traffic with high accuracy by rate limiting traffic based on any parameter of a request.
Protect customer data
Defend against brute force login attacks seeking to take over accounts and steal sensitive information.
Rely on transparent pricing
Avoid unpredictable costs associated with traffic spikes and enumeration attacks. We will not charge you for usage when you are under volumetric attack.
Pick the right option for you
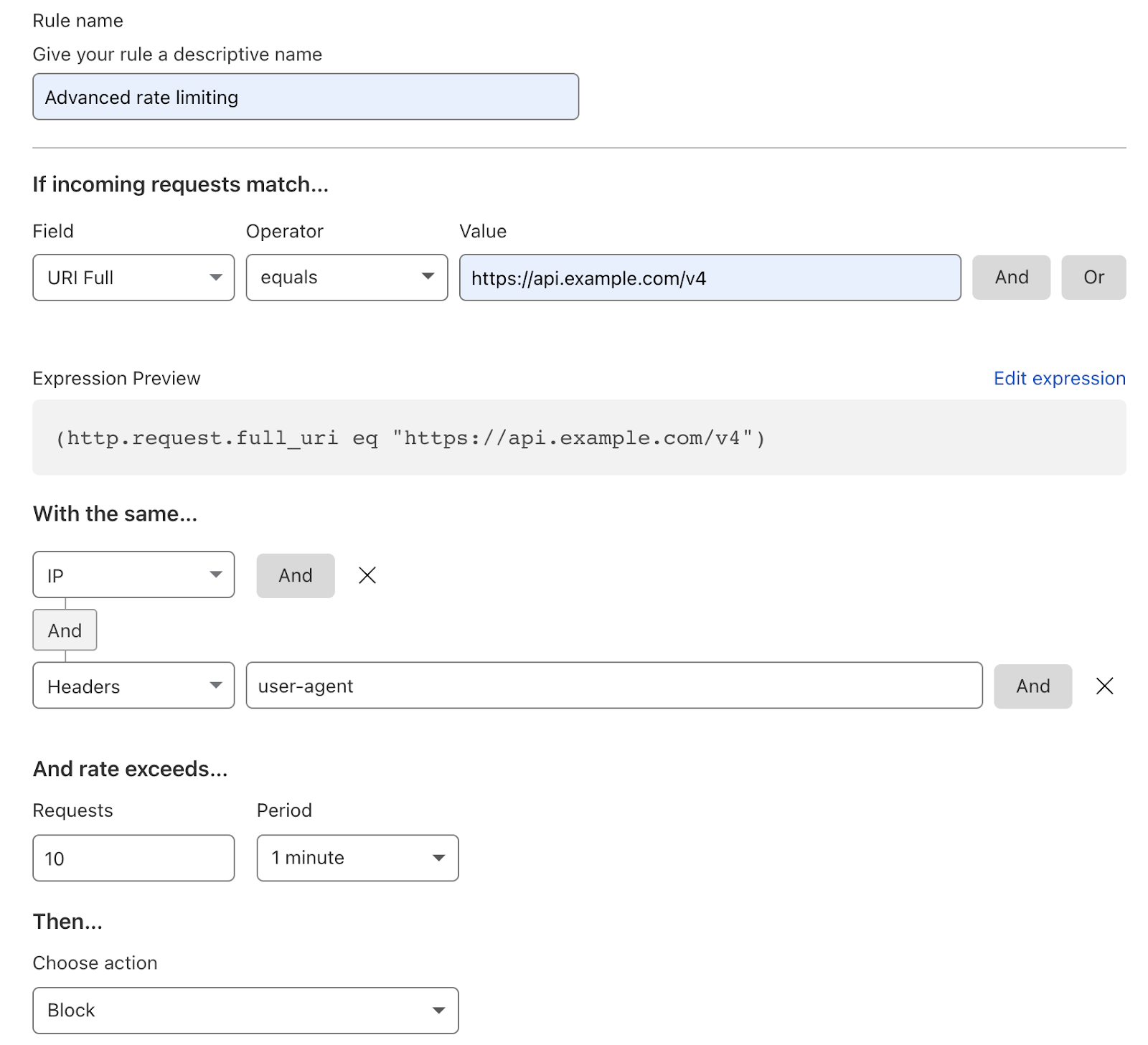
Choose IP-based Rate Limiting to protect unauthenticated endpoints, limit the number of requests from specific IP addresses, and handle abuse from repeat offenders.
Upgrade to Advanced Rate Limiting if you want to protect your APIs from abuse, mitigate volumetric attacks from authenticated API sessions, and take full control of the parameters you rate limit on.

Learn more about rate limiting in our live application security demo series
Gartner® named Cloudflare a Representative Vendor in Web Application and API Protection
Cloudflare has been recognized as a Representative Vendor in the Gartner Market Guide for WAAP report. We believe this recognition validates that we protect against emerging threats faster, offer tighter integration of security capabilities, and deliver powerful ease of use and deployment.
What our customers are saying
“When other companies experienced a data leak, the attackers would often try the stolen email and password combinations on our sites. We always knew when there was another attack, but it was business as usual because Cloudflare detected and stopped it before it became a problem.”
Conrad Electronic
Top Rate Limiting use cases
Configure thresholds
Protect your website URLs and API endpoints from suspicious requests that exceed defined thresholds. Granular configuration options include status codes, specific URLs, request limits, and request methods.
Define responses
Visitors hitting defined request thresholds can trigger custom responses, including mitigating actions such as challenges or CAPTCHAS, response codes, timeouts, and blocking.
Get insights into traffic patterns
Scale and protect your resources with analytics including the amount of malicious traffic blocked by rule and the number of requests that reach your origin.
Helping organizations bolster their application security strategies

