What is the principle of least privilege?
The principle of least privilege ensures that users only have the access they truly need, reducing the potential negative impact of account takeover and insider threats.
Learning Objectives
After reading this article you will be able to:
- Define the principle of least privilege
- Understand how applying this principle improves security
- Understand how this principle relates to Zero Trust security
Related Content
Want to keep learning?
Subscribe to theNET, Cloudflare's monthly recap of the Internet's most popular insights!
Copy article link
What is the principle of least privilege?
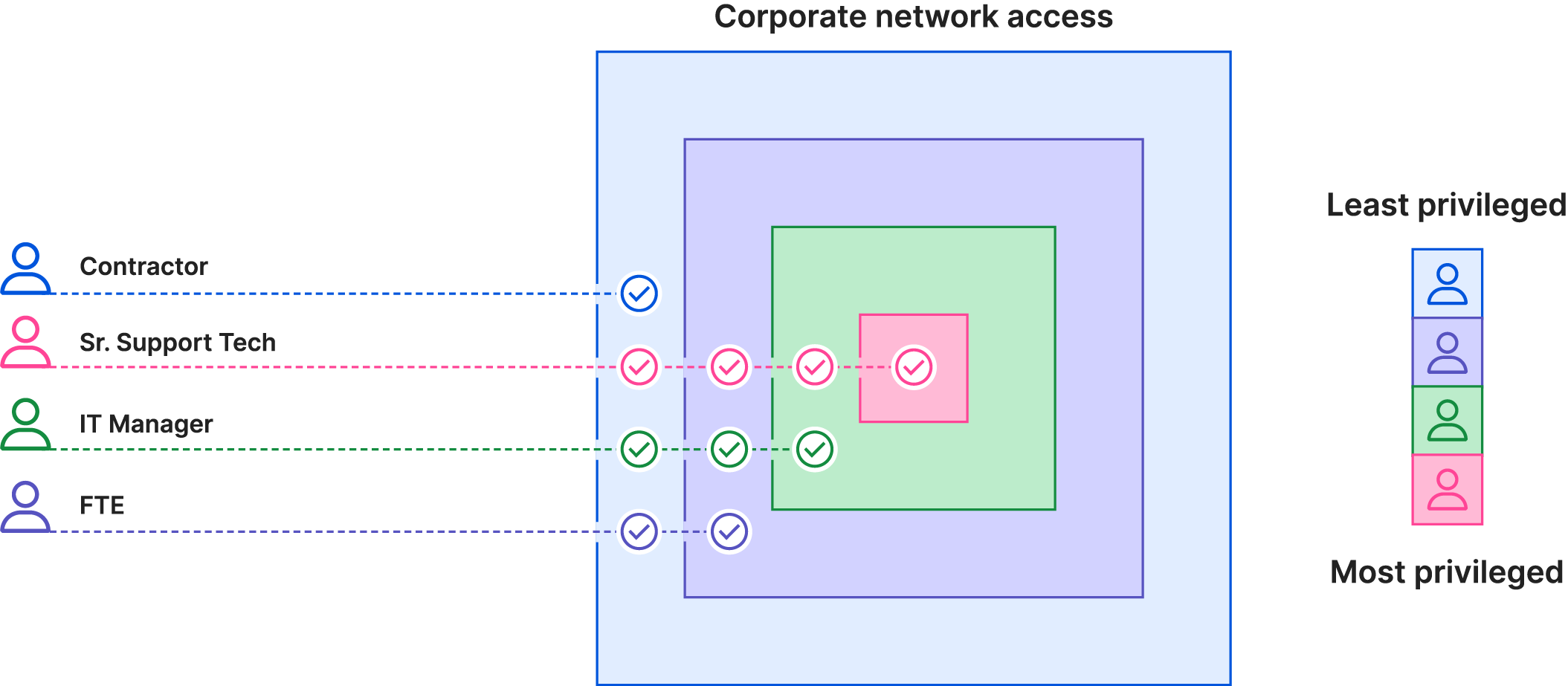
The principle of least privilege, also called "least privilege access," is the concept that a user should only have access to what they absolutely need in order to perform their responsibilities, and no more. The more a given user has access to, the greater the negative impact if their account is compromised or if they become an insider threat.
While the principle of least privilege applies in a wide variety of settings, this article focuses on how it applies to corporate networks, systems, and data. This principle has become a crucial aspect of enterprise security.
As an example: A marketer needs access to their organization's website CMS in order to add and update content on the website. But if they are also given access to the codebase — which is not necessary for them to update content — the negative impact if their account is compromised could be much larger.
How does the principle of least privilege increase security?
Suppose Dave moves into a new house. Dave creates two copies of his house key; he keeps one for himself and gives a backup to his friend Melissa for emergencies. But Dave does not create 20 copies of his key and give one out to each of his neighbors. Dave knows this is much less secure: one of his neighbors might lose the key, accidentally give it to an untrustworthy person, or have the key taken from them, with the result that someone uses the lost key to sneak into his house and steal his expensive television.
Similarly, while a company may not have an expensive television, it certainly has valuable data that it wants to keep safe. The more access the company allows to that data — the more "keys" it gives away — the greater the odds that some malicious party will steal a legitimate user's credentials and use them to steal that data.
How does the least privilege principle relate to Zero Trust security?
Zero Trust security is an emerging security philosophy that assumes that any user or device may present a threat. This contrasts with older security models that consider all connections from inside an internal network to be trustworthy.
The principle of least privilege is one of the core concepts of Zero Trust security. A Zero Trust network sets up connections one at a time and regularly re-authenticates them. It gives users and devices only the access they absolutely need, which better contains potential threats inside the network.
For instance, a non-Zero Trust approach might be to require connecting to a virtual private network (VPN) in order to access corporate resources. However, connecting to a VPN gives access to everything else connected to that VPN. This is often too much access for most users — and if one user's account is compromised, the entire private network is at risk. Attackers often can move laterally within such a network fairly quickly.
The principle of least privilege takes a more granular approach to access control. Each user might have a different level of access, depending on what tasks they need to perform. And they can only access the data they need.
Suppose Dave gives Melissa the backup key to his house but does not want her to view his private documents in his filing cabinet. Since the front door and the cabinet have different locks, he can give her a key to the house without giving her access to the filing cabinet.
This is akin to the least privilege principle: Melissa has only the access she needs to be able to unlock Dave's house if necessary. But using a VPN for access control is like using the same key for both the front door and the filing cabinet.
How to implement least privilege access
Setting up a Zero Trust network enables organizations to put the principle of least privilege into practice. One of the core technical implementations of Zero Trust is called Zero Trust Network Access (ZTNA) — learn more about the nuts and bolts of how ZTNA works.
Cloudflare Zero Trust is a platform that enables companies to quickly implement a Zero Trust approach for network security. Read more here.